Introduction
In today's digital landscape, securing sensitive data is more crucial than ever. BitLocker, Microsoft's built-in disk encryption tool, offers a robust solution to protect data from unauthorized access. By integrating BitLocker with Microsoft Intune, IT administrators can efficiently enforce encryption policies, ensuring compliance and data security across an organization's device fleet. This guide provides a step-by-step approach to configuring BitLocker with Intune, making encryption deployment seamless and manageable. When paired with Microsoft Intune, organizations can seamlessly manage and enforce BitLocker policies across their fleet of devices, ensuring compliance and security.
In this guide, we will walk through the steps to deploy, configure, and monitor BitLocker encryption using Microsoft Intune.
Prerequisites
Before configuring BitLocker policies in Intune, ensure the following:
- Devices should nowadays be Azure AD joined and therefore running Windows 10/11 Pro, Enterprise, or Education editions.
- TPM 2.0 is recommended (though BitLocker can work without it using a password-based approach).
- Microsoft Intune is properly set up and configured and ready to create our policies
Now - Let’s jump right in!
🎯 Goals
The goal of this blog post is to provide IT administrators with a clear, step-by-step guide for configuring BitLocker using Microsoft Intune.
By the end of this blog post, you should be able to:
- Understand the importance of BitLocker encryption and how it enhances data security.
- Create and deploy a BitLocker policy in Intune to enforce encryption on organizational devices.
- Verify encryption status and recovery key storage to ensure devices are compliant and securely managed.
🧩 Use Case
A financial services firm, needs to protect sensitive client data across its remote workforce. The IT team wants to ensure that all employee laptops are encrypted without requiring manual intervention.
Example Use Case:
- Industry: Corporate, there is no explicit industry - should be implemented at every organization
- Challenge: Encrypting the Disks with Intune
- Goal: Create and deploy a BitLocker policy in Intune to enforce encryption on organizational devices.
Why does this matter? BitLocker provides several key functionalities to enhance device security:
- Full Disk Encryption – Encrypts entire drives to protect data from unauthorized access.
- TPM Integration – Uses Trusted Platform Module (TPM) to securely store encryption keys.
- Pre-Boot Authentication – Optional feature requiring a PIN or USB key before booting.
- Network Unlock – Allows automatic unlocking of BitLocker-protected devices in a corporate network.
- BitLocker To Go – Extends encryption to external USB drives for portable security.
- Recovery Key Management – Securely stores recovery keys in Azure AD or Active Directory for easy retrieval.
- Silent Encryption – Enables encryption in the background without user intervention.
- Compliance Reporting – Provides encryption status monitoring through Microsoft Intune.
⚙️ Technical Description
BitLocker is a highly technical security feature that requires a deep understanding of encryption, key management, and system security. For those looking for a detailed, behind-the-scenes breakdown of BitLocker, Anoop C. Nair has written an extensive analysis on how BitLocker works under the hood. You can read his in-depth article here: BitLocker Unlocked – Behind the Scenes Windows 10.
This guide focuses on the practical implementation of BitLocker with Microsoft Intune, ensuring IT administrators can efficiently enforce encryption policies and enhance device security.
🔧 Step 1: Intune Configuration
There are two ways you can configure the Bitlocker policy - Either over the Settings Catalog where you have to select the settings yourself or through Endpoint Security > Bitlocker. At this point I recommend you to go through the Endpoint Security Setting, as its more straight forward and gathers the configurations of the settings catalog:
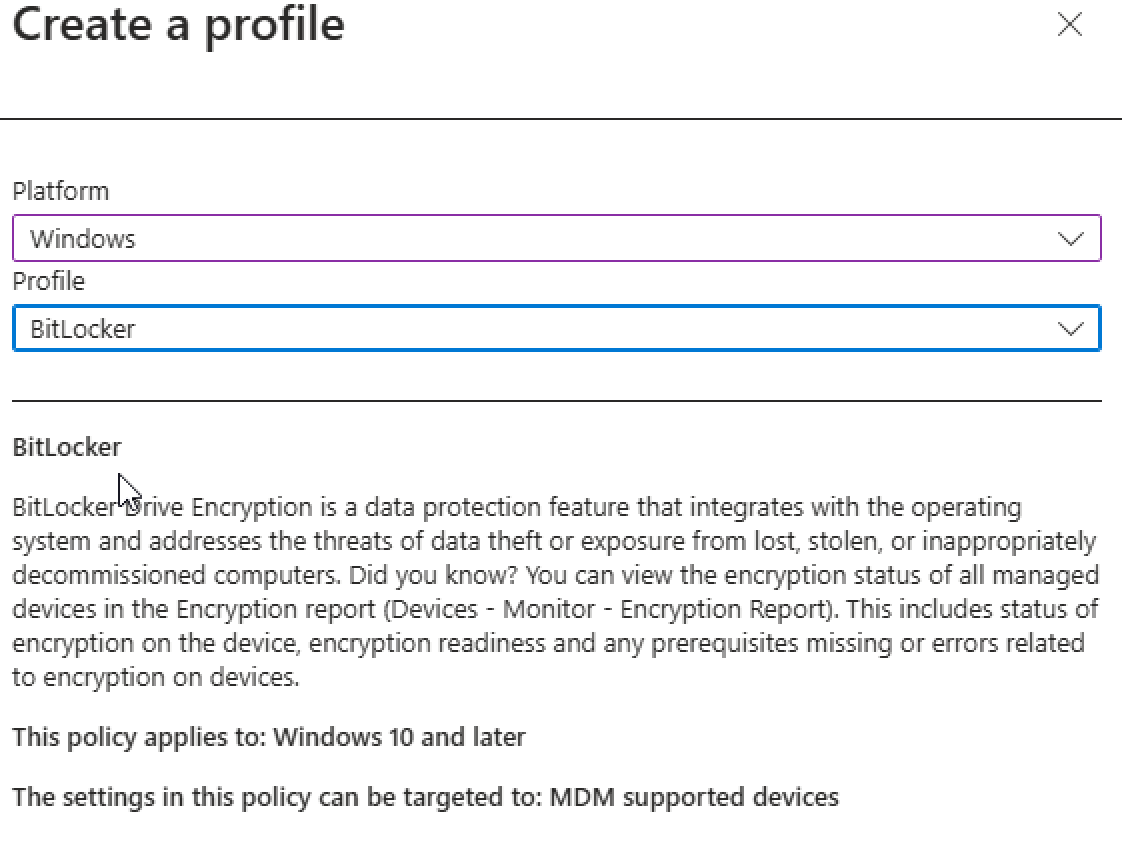
Now lets get into the profile - as operating System select Windows and as the profile select Bitlocker. After that name you want to give the configuration (you will then see this configuration in the device configurations as well). In this case we use EndpointSecurity-Bitlocker.
After that we now dive into the configuration:
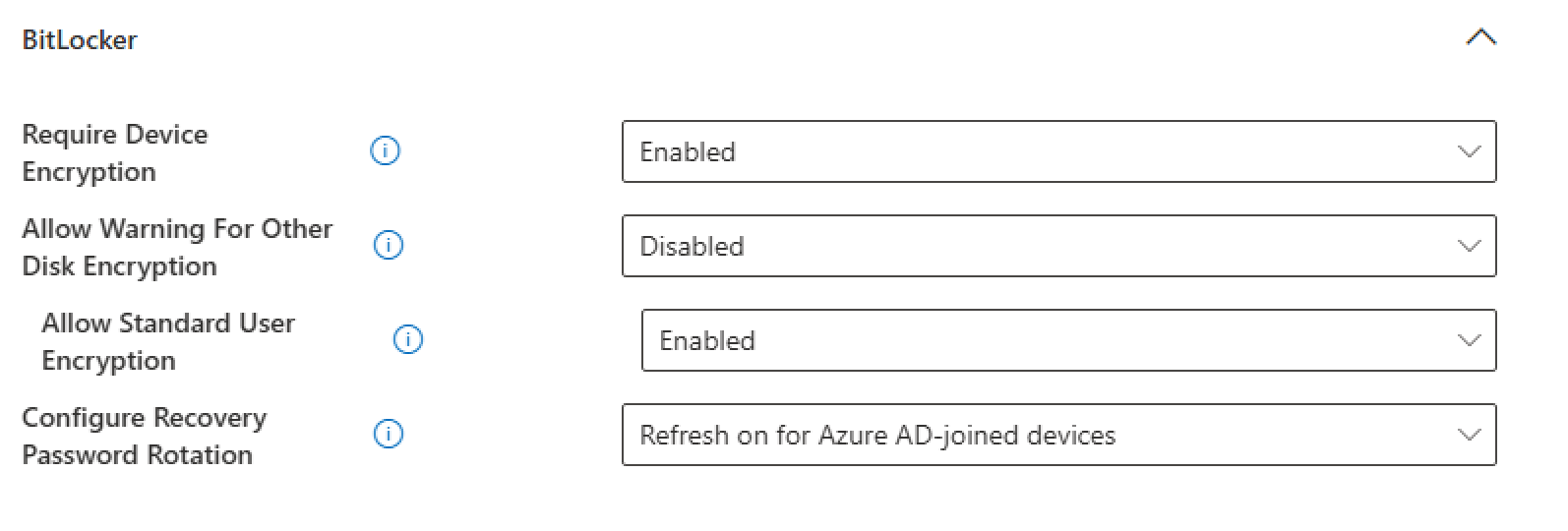
Bitlocker
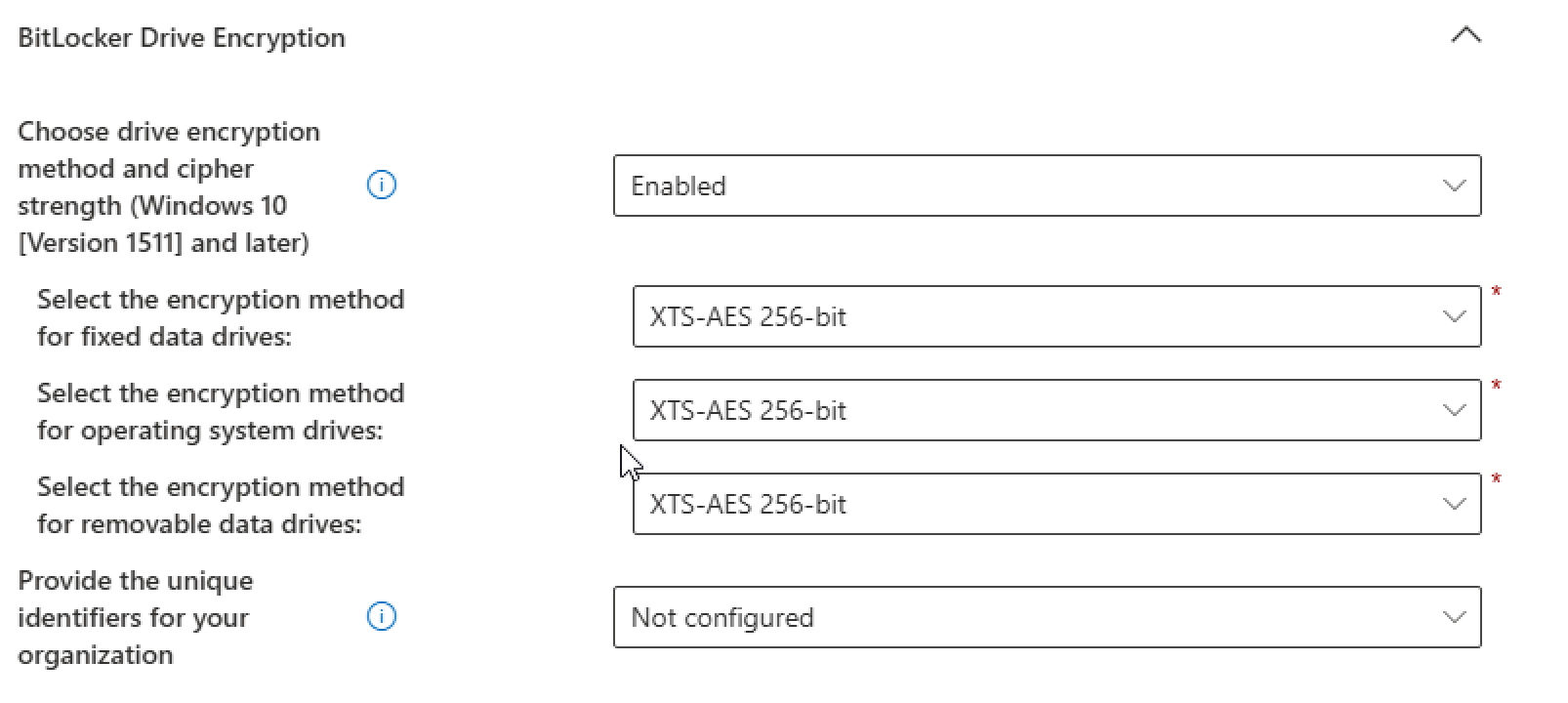
Bitlocker Drive Encryption
Operating System Drives
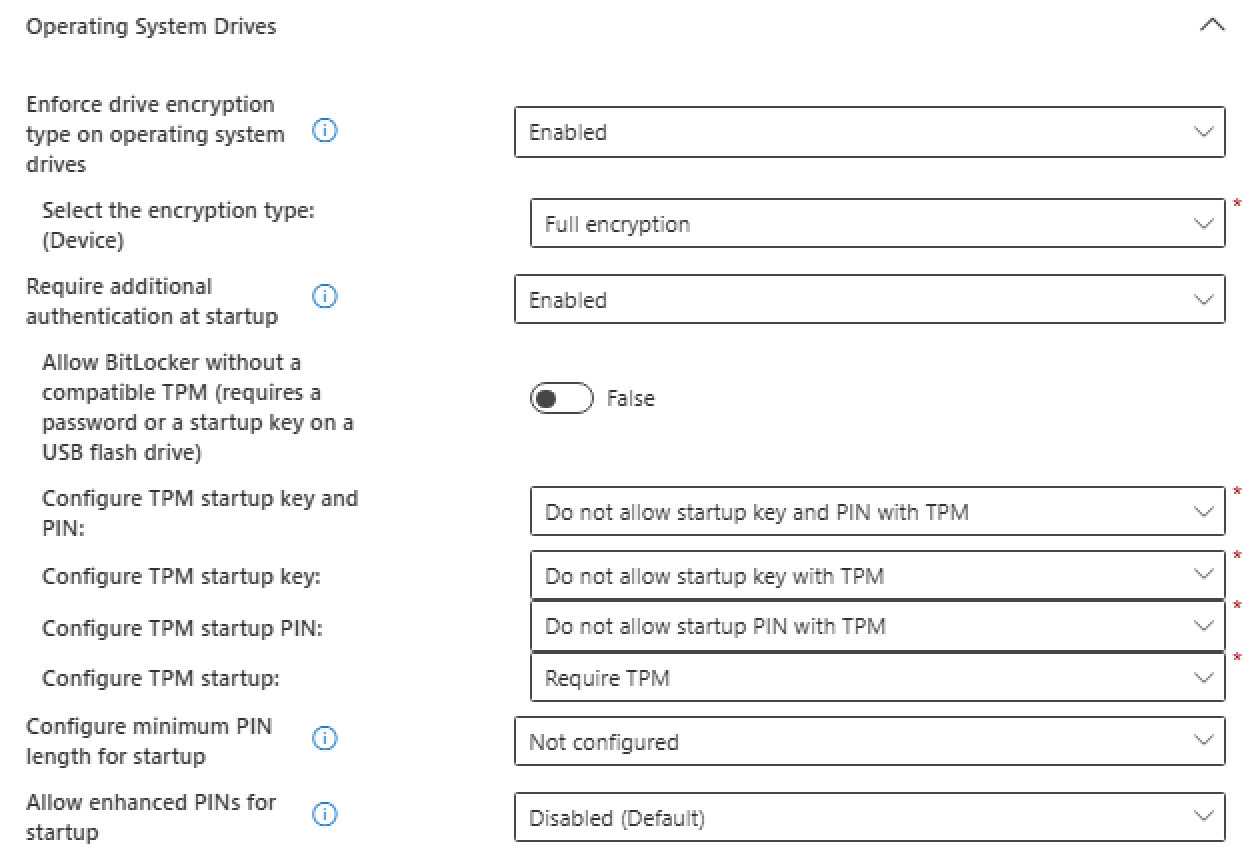
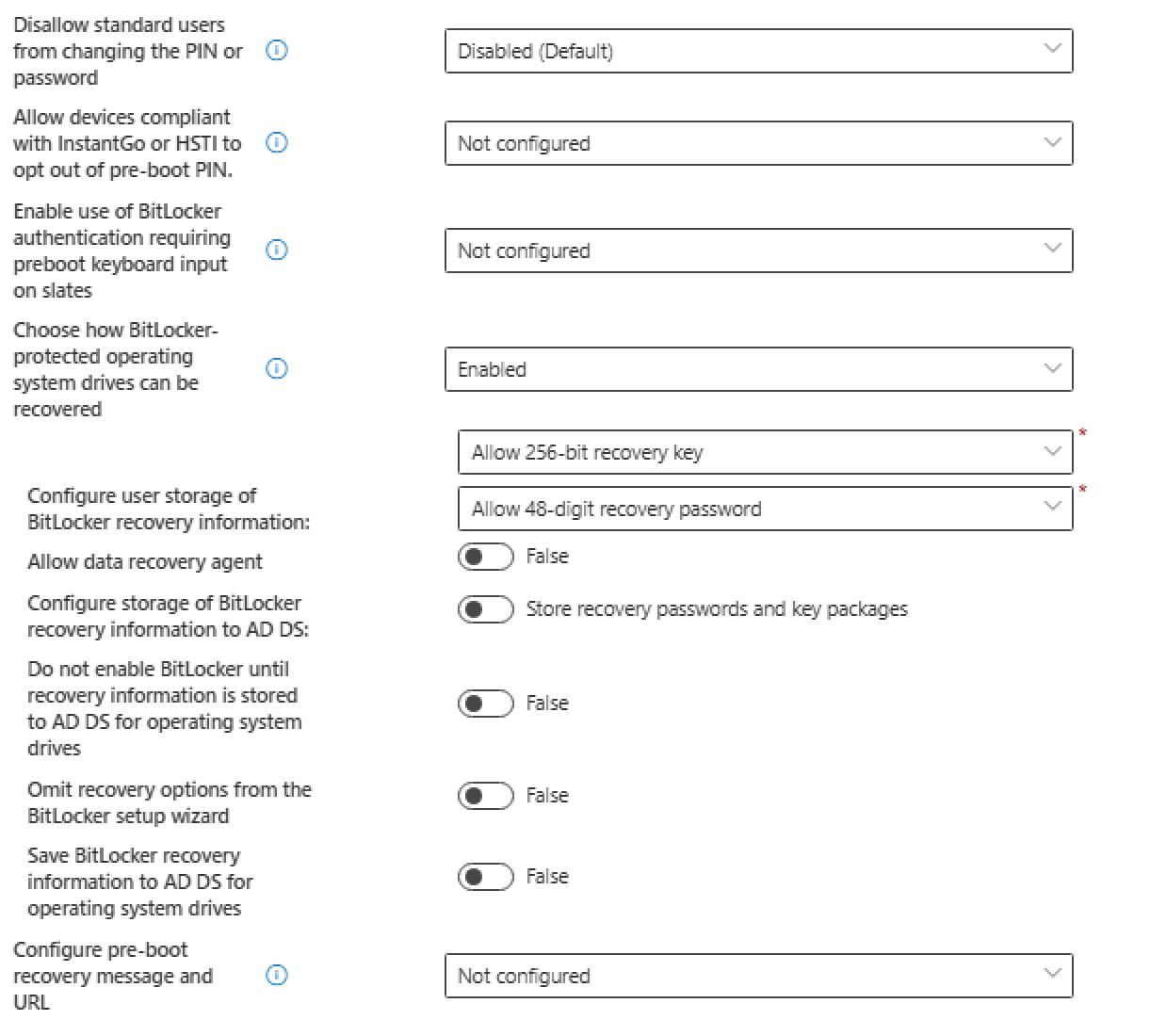
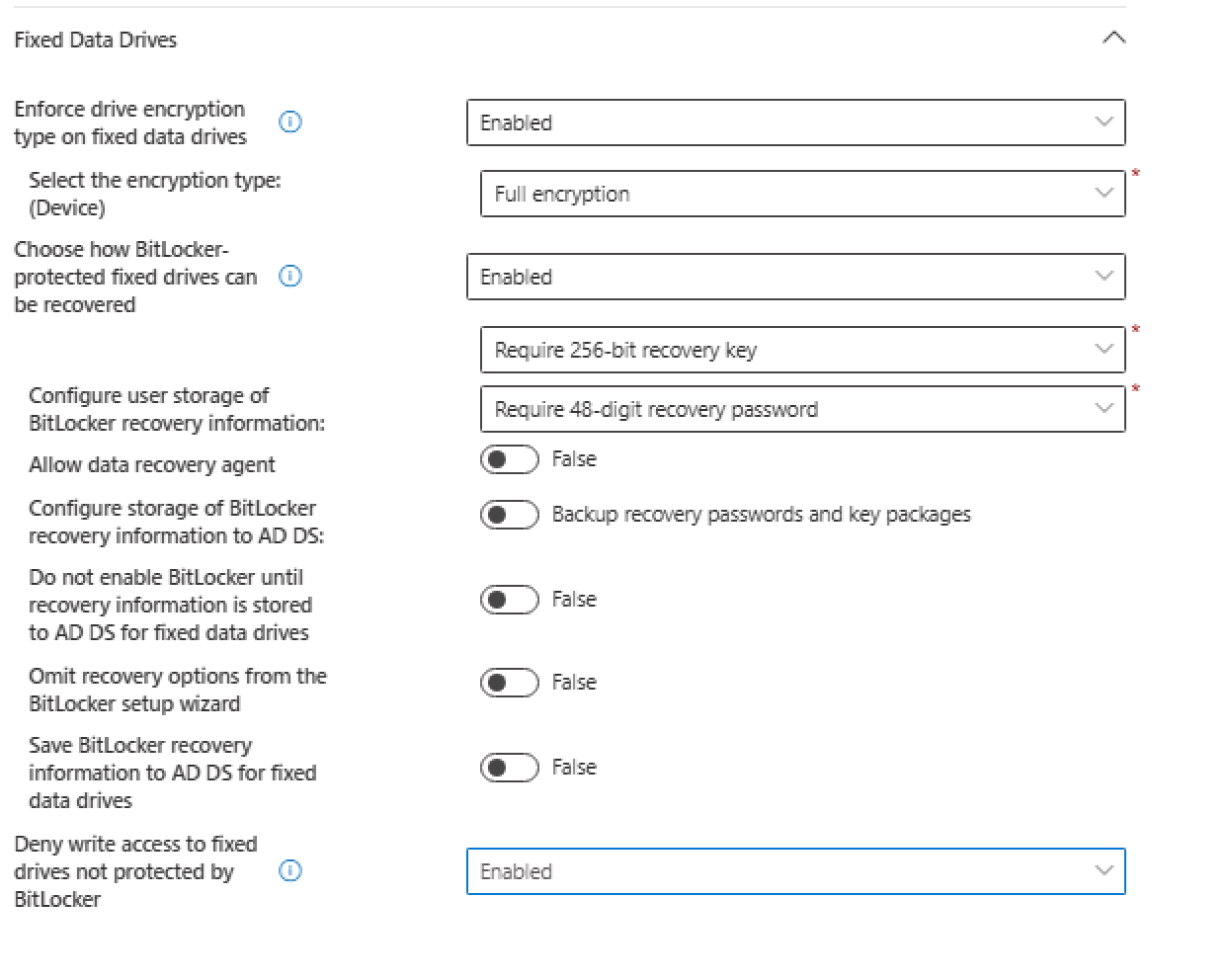
Fixed Data Drives
Thats it - now assign it to your desired group or to All Devices and give it some time to sync.

In the meantime lets have a quick look into what we have actually configured with those settings:
- We require device encryption mandatory
- Disabled the warnings for the user
- Configured the rotation of the Recovery Password
- Choosed a strenght encryption method: XTS-AES 256-bit
- We selected the full encryption of the OS Disk (C:)
- We dont allow a startup PIN to be set for daily use for the users
(But can make sense for some devices which needs high security) - We require TPM
- We requre Bitlocker for fixed data drives
- We do not store the informations to the AD DS
🔎 Validation and Testing
Once you've created the policy and gave it some time to set those settings you now can navigate to a device > Recovery Keys, where you pointed the settings to:
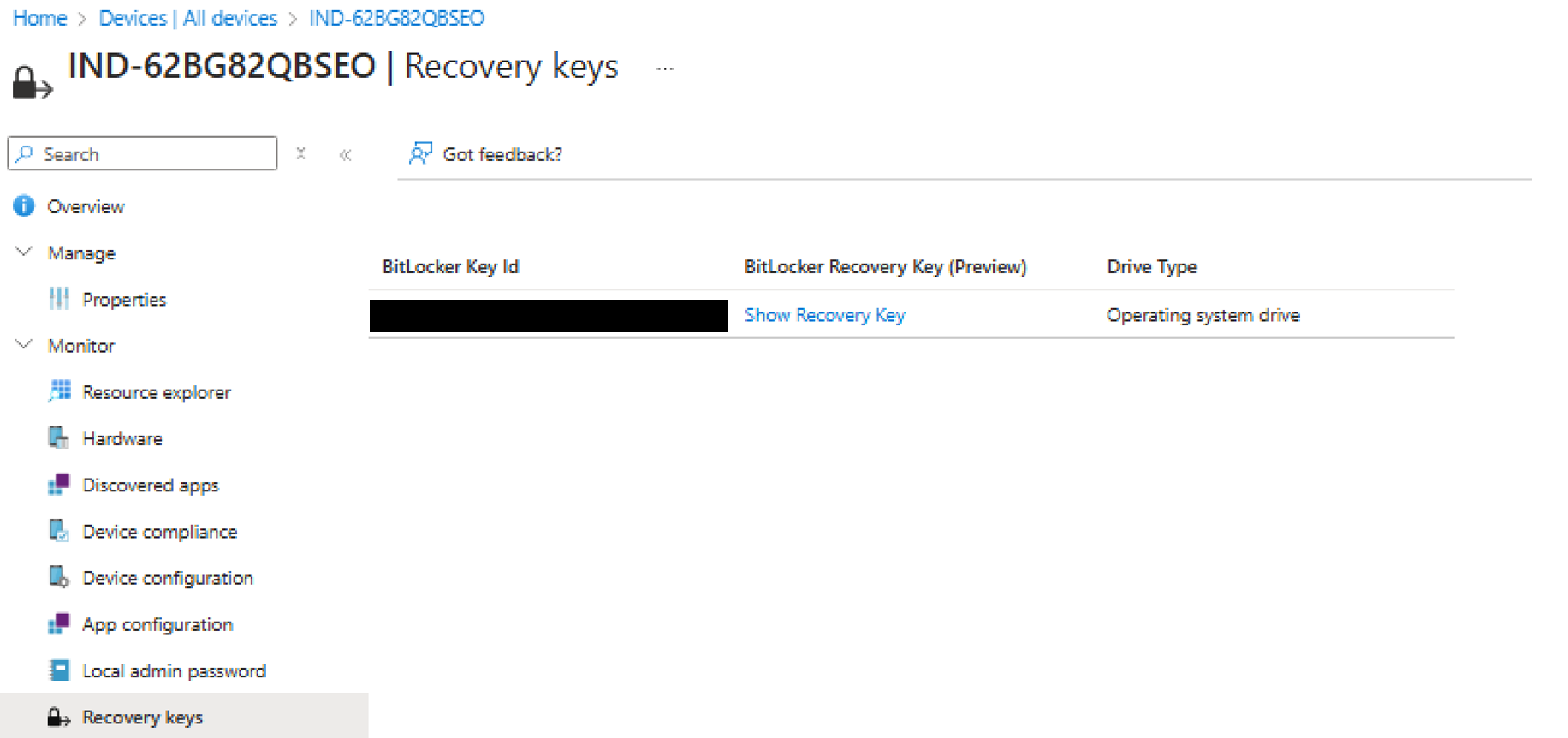
Now verify, that you are seeing the recovery key, when you navigate to Show Recovery Key.
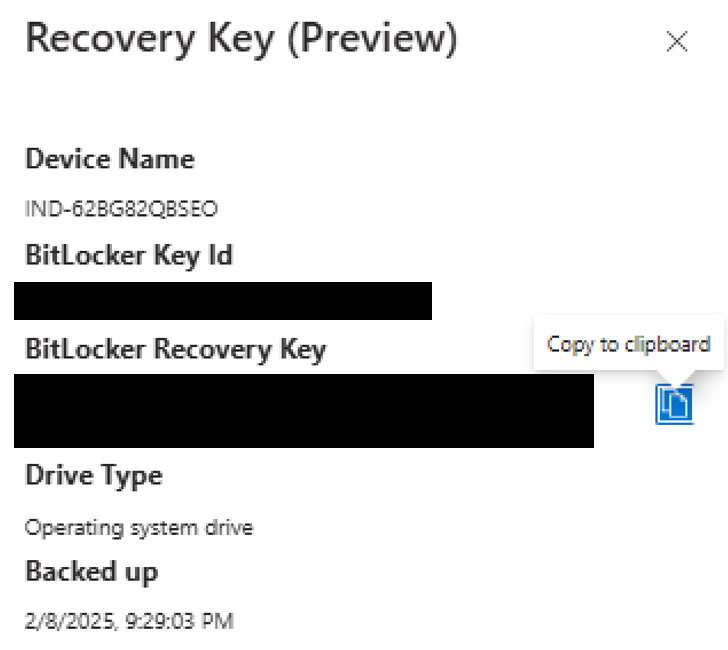
On the Windows device you should see under the Bitlocker settings, that Bitlocker has been activted and that the settings are managed:

Compliance Policy
For a little + on this Blog I included the configuration of the compliance policy which we use when we configure Intune for customers:
I recommend you to create a compliance policy e.g. Compliance-DHA which checks only the device health and than assigning that to all devices:
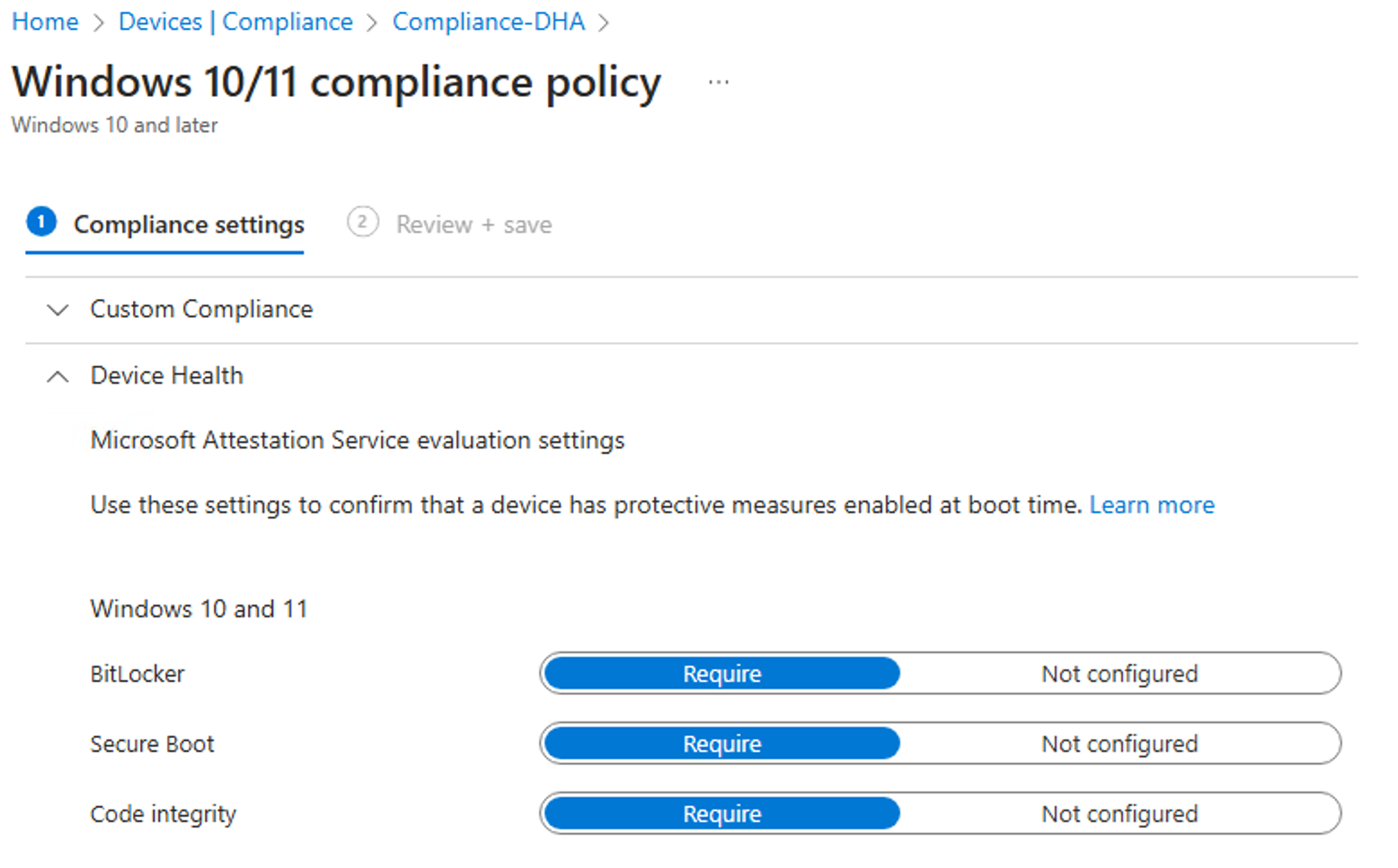
After this one you can create another compliance policy for your needs. So you have a more granulare control over the compliance of your organization.
📝 Summary
Let’s recap what we covered in this post:
- Intune Settings Catalog configuration for a strong Bitlocker deployment
- Verifying the functionality of Bitlocker
- Verifying the compliance of the device
This blog post highlights how Intune simplifies BitLocker deployment, ensuring seamless encryption management for organizations. It emphasizes security, compliance, and ease of use, making it an essential tool for IT administrators handling Windows devices.
⚠️ Disclaimer
The configurations shared in this post reflect my personal approach to solving this specific challenge. Every environment is unique, so adapt these solutions to fit your needs.
Happy configuring! 😊




